Security organisations have observed a significant increase in attacks by criminal hackers who are attempting to take advantage of the extraordinary circumstances the COVID-19 crisis presents. They have observed an increase in scams and phishing attempts related to COVID-19. Phishing is a fraudulent scamming attempt to obtain sensitive information from an end user (for example, username, passwords, and credit card information). For example, by asking a user to click on a link that results in malicious software being installed.
Entities need to ensure they implement effective security controls to support their employees working from home. Employees working from home need to be vigilant to maintain the security of their entities’ systems and information.
Working from home
Among many other things, COVID-19 has brought about a fundamental change in how we work. Working from home brings the obvious challenges of untrusted networks and insecure residential environments, but it also poses a less obvious threat – letting our guard down.
Entities should remind staff to lock computers when not in use and not to leave sensitive information laying around. They should also ensure staff can log in securely to their systems, use strong passwords, and be vigilant when reading emails (which are in increased use during this time and can expose entities to phishing attacks).
Multi-factor authentication
To support employees to work from home securely, entities should ensure they enable multi-factor authentication to prevent users from remotely logging into an entity’s internal network without requiring two-factor authentication (for example, a username and password plus a code sent to a mobile phone). This makes it much harder for cyber criminals to compromise sensitive information and systems.
Passwords
Entities should ensure they make their staff aware of their responsibilities in managing cyber risks. Poor password practices unnecessarily expose entities to attack. Easily guessable passwords make it simpler for hackers to compromise user accounts and use these accounts to gain control over an entities' networks. In our report Managing cyber security risks, which tabled in parliament in October 2019, we recommended that entities:
| undertake a risk assessment to determine the most effective password policy and implement it as a priority | |
Controls may include:
|
Risks with emails
Entities should alert their employees to continue to use professional scepticism and exercise caution if they receive an email that is unexpected or looks a little unusual.
The best protection is awareness and detection. Employees should not open attachments or click links in unsolicited emails – if the email is unexpected, they should be wary of opening the attachment and always verify the link.
Entities should demonstrate to staff how to identify and report phishing emails and other threats.
Here are several tell-tale signs of a phishing scam:
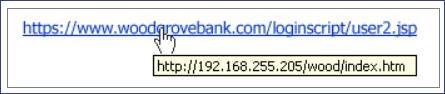
- The links or URLs provided in emails are not pointing to the correct location or are attempting to get you to access a third-party site that is not affiliated with the sender of the email. For example, in the image below, hovering over the link provided shows it doesn’t match the URL that you will be taken to.
- There is a request for personal information such as personal information or bank or financial information. Official communications won't generally request personal information from you in the form of an email.
- Items in the email address will be changed so that it is similar enough to a legitimate email address but has added numbers or changed letters.
- The message is unexpected and unsolicited. If you suddenly receive an email from an entity or a person you rarely deal with, consider this email suspect.
- The message or the attachment asks you to enable macros, adjust security settings, or install applications. Normal emails will not ask you to do this.
- The message contains errors. Suspicious messages may have typographic or grammatical errors or contain wrong information, or inconsistencies or things that are not quite right such as outdated logos or typos.
- The sender address does not match the signature on the message itself. For example, an email is purported to be from Mary of Contoso Corp, but the sender address is john@example.com.