Overview
Information technology (IT) systems underpin government services and are a vital component of the state's assets. Entities need to actively manage these systems to maintain them and keep them secure.
Through our information systems audit program, we form opinions about the security and integrity of key IT systems to ensure financial data can be relied upon for financial reporting.
Tabled 3 December 2025.

Report on a page
This is our first report on information systems controls, designed to recognise the collective need across government for more focus on the security of information. This report provides:
- a summary of matters identified in our information systems audits for state entities in Queensland’s public sector
- preliminary insights on legacy systems that have passed their lifespan and are no longer supported by their technology providers.
Queensland public sector entities include the 21 core departments (referred to as ‘departments’ in this report), statutory bodies, and government owned corporations.
IT system defences need strengthening |
While entities generally have effective IT controls for finance systems, control deficiencies remain in:
- system access (controlling who can access which part of systems)
- passwords and authentication (verifying that only authorised users can access systems)
- security configuration (checking allowable and required actions to access systems)
- detective controls to identify potential incidents
- managing risks associated with third parties.
Entities are not fully tackling root causes due to competing priorities and are not checking that implemented controls are effective. A significant number of deficiencies remain unresolved from prior years, suggesting that entities are not addressing IT risks in a timely way.
Entities need greater focus on:
- strengthening IT systems defence to address control deficiencies that continue to exist
- addressing IT systems deficiencies from prior years to close security gaps.
Half of finance systems are being used beyond their lifespan |
Half of the systems we audited for financial reporting purposes are legacy systems being used well beyond their expected lifespan and are no longer supported by technology providers. Entities often need to implement manual workarounds and may be unable to implement security updates. This impacts effective operation of controls and the efficiency of entities’ operations, and creates security risks.
Departments, as part of their annual report to the Department of Customer Services, Open Data and Small and Family Business, reported increases in at-risk systems, which require attention. The accuracy, quality, and completeness of data reported about at-risk systems suggest there is not a complete understanding of the extent of these legacy systems, the cost to replace those systems, and IT asset management practices.
Departments need to continue to accurately and completely report on at-risk systems and their register of IT assets.
For entities embarking on new system implementations, we have provided key considerations for those with governance oversight responsibilities for projects and accountable officers for assessing the effectiveness of controls in Appendix D.

1. Recommendations for entities
We have not made any new recommendations in this report.
We made recommendations to remedy control deficiencies to the individual entities we audited.
We did not make any new recommendations in State entities 2024 (Report 11: 2024–25). Instead, we drew entities’ attention to the recommendations from State entities 2023 (Report 11: 2023–24) that require further action.
For a full list of the recommendations from previous years and their status, see Appendix C.
Reference to comments
In accordance with s. 64 of the Auditor-General Act 2009, we provided a copy of this report to relevant entities. In reaching our conclusions, we considered their views and represented them to the extent we deemed relevant and warranted. Any formal responses from the entities are at Appendix A.

2. Information technology controls at state entities
Information technology (IT) systems underpin government services and are a vital component of the state's assets. As with any asset, IT systems need active management to maintain them and keep them secure. Entities increasingly use third-party, internet-based technologies (for example, cloud systems) to deliver computing services.
As part of our financial audit role for state entities, we audit key IT systems relevant for financial reporting. These systems record entities’ financial transactions and balances.
This chapter details the results of our 2024–25 audits and discusses state entities’ progress in addressing control deficiencies identified in prior years.
Chapter snapshot
Greater attention is needed to strengthen IT systems defence
A cyber security breach is recognised globally as a key enterprise risk. The impact of a cyber security breach includes business loss or disruption and compromise of systems and data. This can have reputational, financial, and legal implications for the state.
The 2023–24 Annual Cyber Threat Report from the Australian Cyber Security Centre (ACSC) explained that malicious actors are continuing to adapt their approaches in their attempts to compromise Australian organisations. State and local governments had the second-highest number of reported cyber security incidents, after the federal government. The ACSC report can be accessed via www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/annual-cyber-threat-report-2023-2024.
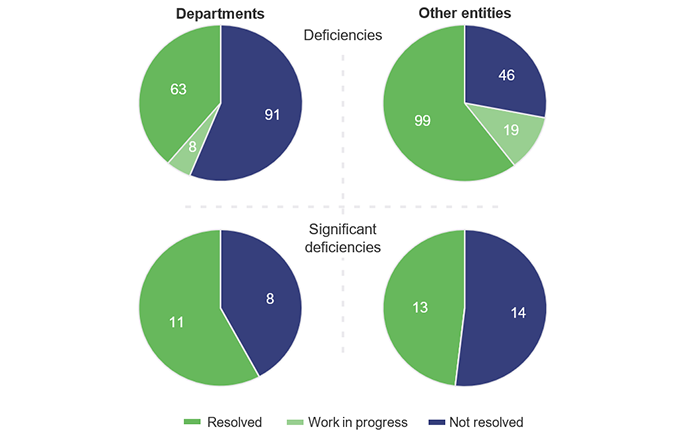
Cyber security risks are increased by deficiencies in IT systems controls. In 2025, we identified 13 significant deficiencies and 198 deficiencies in entities’ IT systems controls. While the number of deficiencies is fewer than last year, almost half of the deficiencies from prior years remain outstanding. This means there are controls that require further attention.
Entities should focus their attention on the following areas where we consistently identify deficiencies:
- system access, including privileged accounts and system accounts security
- passwords and authentication
- security configuration
- detective/monitoring controls
- third-party security risk management.
Figure 2A details what the deficiencies in IT systems mostly relate to.
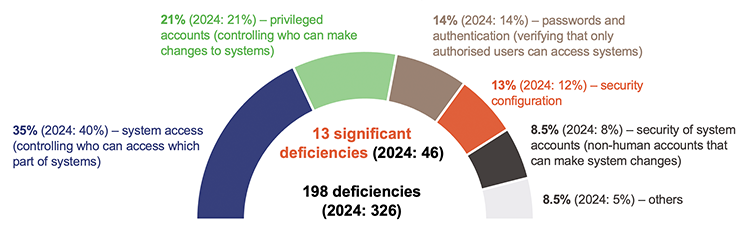
Queensland Audit Office from our 2024–25 audits.
These deficiencies usually occur because:
- entities have not applied their IT security policies and better practices consistently across all their IT systems
- entities implemented new IT systems or made significant changes to their IT environment during the year.
Entities are not checking that system access controls are effective and adequate |
Entities have established processes to ensure only authorised users can access their systems. However, they do not regularly assess whether the established processes for system access are working effectively or whether they cover all aspects needed to manage system access.
System access controls requiring attention include:
- terminated accounts
- dormant accounts
- external or guest accounts
- accounts with privileged access that control who can make changes to the system
- system account security.
Terminated accounts
Entities should:
| Dormant accounts
Entities should:
|
Guest accounts
Entities should:
| Privileged access
Entities should:
|
System accounts
Entities should:
| User access reviews
Entities should perform regular access reviews, ensuring the account and entitlement is required and appropriate. |
Queensland Audit Office from the result of our 2024–25 audits.
Effective password management and authentication are essential controls |
Passwords are often the first line of defence for access to systems. They are the cornerstone of a secure environment, but they can be one of the weakest links when not managed properly.
The Australian Cyber Security Centre recommends multi-factor authentication (MFA) as one of the most effective ways an organisation can protect information and user accounts against unauthorised access. Using MFA, a user enters both a password and a one-time code received to their mobile phone. The ACSC recommendation can be accessed via www.cyber.gov.au/protect-yourself/securing-your-accounts/multi-factor-authentication.
Most entities require MFA for remote access. A small number of entities are in the process of rolling out MFA across their entire user base to strengthen security.
Passwordless authentication relies on either biometric verification (for example, fingerprint or facial recognition) or the use of a personal identification number instead of a traditional password. Passwordless authentication is becoming more prevalent, and several entities use it to simplify and enhance security. Others are in the process of implementing passwordless authentication. This is a positive step to enhance security.
Security configurations require regular updates |
Software providers and the cyber security industry regularly update their technologies and recommendations to make systems more secure and stable. To establish and maintain secure systems, entities document and regularly update their requirements for security configurations. Entities need to implement these updates across their systems.
Some entities review and update their IT governance documents to specify high-level security requirements. However, they often do not:
- implement changes in the updated IT governance documents consistently across all systems
- document their detailed minimum or baseline requirements for security configurations
- perform appropriate and documented risk assessments for implementing alternative controls when unable to implement their required security configurations
- monitor and update their security configurations in line with recommendations from their software providers or the cyber security industry.
Entities need to ensure detective controls are effective |
We evaluate the following security controls:
- preventative – block or prevent security incidents before they occur
- detective – identify and detect potential unauthorised access, security incidents, or policy violations while or after they occur.
Where preventative controls cannot be fully implemented – due to technical limitations, cost, or operational constraints – organisations need to ensure the effectiveness of their detective controls.
Many entities have suitable security event logging, alerting mechanisms, and processes. However, some entities do not have effective detective controls to:
- monitor and alert entities about the use of accounts with full system or elevated access
- detect unusual account logon patterns
- monitor guest or generic user account activity.
Entities need to manage third-party security risks |
Many entities depend on external organisations (third parties) to deliver IT services and technologies. These third parties often have significant levels of access to entities’ systems. Cyber security risks in third parties’ information systems could, therefore, have significant flow-on impacts on the security of state entities’ systems.
Entities often:
- give their information system service providers full access to their systems without checking if it is needed
- do not define their detailed requirements on controls for service providers
- do not regularly verify that service providers have effective cyber security controls in place
- do not have adequate contractual agreements to regularly verify security processes, controls, or notification of cyber security incidents.
In our report State entities 2023 (Report 11: 2023–24), we recommended that all entities manage the cyber security risks associated with services provided by third parties by implementing the 4 processes outlined in Figure 2C.
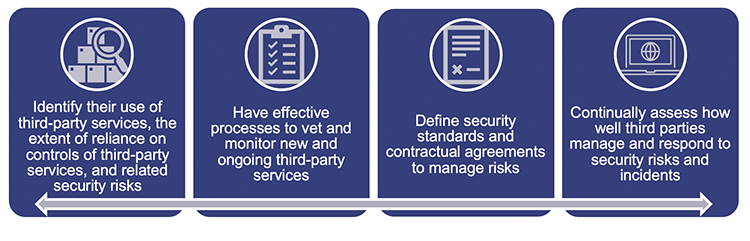
Queensland Audit Office from State entities 2023 (Report 11: 2023–24).
We continue to identify deficiencies in how entities manage cyber security risks with services provided by third parties. The status of the recommendation for managing security risks associated with third parties is in Appendix C.
We have planned a performance audit to be tabled in 2025–26 to assess in more detail how effectively public sector entities manage third-party cyber security risks.
Opportunities for entities – strengthen IT systems defence Entities should:
|
| To better assist entities undertaking system implementations, we have listed key considerations for those with governance oversight responsibilities for projects and accountable officers to assess the effectiveness of associated controls in Appendix D. |
More attention is needed to address outstanding deficiencies
The number of new deficiencies we reported in 2025 was 43 per cent lower than in 2024. However, almost half (43 per cent) of the deficiencies identified in prior years remain unresolved.
Entities have not resolved deficiencies from prior years in line with their committed resolution dates.
Departments have addressed some of the significant deficiencies in IT systems we identified last year. Reasons provided for extending the time frames to resolve the deficiencies include:
- complexity of the systems, which require additional time for resolution
- re-alignment of activities with other security improvements or corporate projects to provide a more holistic resolution of deficiencies
- implemented measures that require further work due to the complexity and size of the entities.
For other entities, 57 per cent of significant deficiencies requiring urgent attention have remained outstanding for more than 2 years.
Slow resolution of significant deficiencies by other entities is due to:
- staff turnover and organisation restructures, which result in loss of skills and knowledge
- ineffective governance of third-party service providers to address and monitor the resolution of security deficiencies
- security measures that were implemented but did not fully address the deficiencies identified.
Figure 2D compares the resolution of prior year issues between departments and other entities.
Queensland Audit Office from the results of our 2024–25 audits.
Opportunities for entities – address IT systems deficiencies Entities should:
|

3. Legacy systems
Entities use information technology (IT) systems for many critical functions. These systems enable entities to deliver services, collect revenues, and manage assets and expenditure.
Entities often continue to use legacy IT systems and extend their use beyond the average lifespan of 10 years. Some technology providers cannot provide maintenance and security updates to systems beyond their lifespan. Legacy systems often cannot support new requirements or interact with newer systems.
This chapter focuses on the legacy systems departments use, and provides information about activities to address the risks of continuing to use legacy systems.
Chapter snapshot
Half of the systems we audited are legacy systems
We audited 57 IT systems that departments use, including both finance and business systems that process transactions considered material for reporting financial statements. Half of these systems are being used beyond their lifespan.
Technology providers no longer provide maintenance and security updates, meaning that the systems have the following limitations:
- an inability to implement password configurations in line with organisational IT security policies or better practices
- an inability to implement security patches because the relevant software providers have stopped issuing updates
- incompatibility or difficulty integrating with other, more modern IT systems, such as the systems used for privileged access monitoring
- a need for workarounds or an inability to implement efficient or effective controls due to system limitations. For example, some systems cannot capture a register of users’ activities and, therefore, entities cannot implement controls to detect unauthorised activities.
Where possible, departments implement mitigating controls; otherwise, they need to accept the risks for continued use of these systems.
These unmanaged risks mean that departments are exposed to potentially unauthorised access to legacy systems. Such access can go undetected and result in fraud, error, or information leakage.
Departments are currently upgrading a key finance system
Departments use SAP ECC6 as their key financial system. Mainstream support provided by SAP for ECC6 will end in December 2027, with a negotiable option to extend maintenance until December 2030. The extended support, if required, will be at an increased cost.
Queensland Shared Services (QSS) hosts SAP ECC6 instances on behalf of most departments and is upgrading to a newer version of this system, S/4HANA. QSS will upgrade the system for departments between May and December 2026, except for the 5 departments which host their own instances. Three of those 5 departments have already migrated to S4/HANA, and the others are in the process of upgrading.
Departments are responsible for managing other key business systems for their operations, such as revenue systems and asset management systems.
Government does not have a reliable inventory of legacy systems
To effectively manage risks associated with systems, departments need an accurate and complete inventory of all systems, including legacy systems that are at or nearing the end of life. The Department of Customer Services, Open Data and Small and Family Business (CDSB) also needs this information to coordinate a whole-of-government response to legacy systems and manage other strategic activities.
CDSB’s Queensland Government Chief Information Office (QGCIO) has been collecting information about at-risk systems, which should include legacy systems, from departments since 2012. This information is updated bi-annually. CDSB also collects other information from departments, including the following datasets:
- IT resources – collected annually in June to list all systems in use by departments
- digital projects dashboard – collected every 4–6 weeks, with an 8-week maximum, to provide a publicly accessible dataset about digital projects across departments.
The information across the 3 datasets is not consistent, including those systems listed as at-risk. While CDSB collects the datasets for different purposes, the inconsistencies make it difficult for it to assess:
- how departments manage the IT systems throughout their useful lives
- how well departments plan to upgrade or replace systems
- opportunities for CDSB to coordinate upgrades and replacements across departments
- how IT investments address the risks of legacy systems.
The government needs accurate and complete information about systems to manage risk and to estimate the current cost of replacing legacy systems. Information differs across datasets due to risk assessments, accuracy, and timeliness of updates.
Departments assess risk in an inconsistent way
Each department identifies systems to include in the at-risk dataset based on its own risk assessments. While CDSB provides and updates the standards, examples, and guidance, departments do not have a common approach to categorising risk levels.
Figure 3A highlights an example of how changing departmental risk assessments affect the reported at-risk systems.
| Impact of risk assessment to at-risk systems reporting |
|---|
TRAILS (Transport Registration and Integrated Licensing System) managed by the Department of Transport and Main Roads TRAILS is a key application used by the Department of Transport and Main Roads (TMR) since 1993 to manage driver licences, vehicle registration, and traffic offences. In February 2024, the then Minister for Transport and Main Roads reported that more than 4 million licences and nearly 6 million registrations were issued through the system each year. A 2012 QGCIO report noted that TRAILS would reach its end of life in 2017 and cost $60 million to replace. Between 2018 and early 2024, the government spent more than $7 million in scoping, due diligence, project planning, and market engagement for registration and licensing modernisation. In February 2024, the government:
After the 2012 assessment that the system would reach its end of life in 2017, TMR assessed the risk of the system 3 times:
TMR advised that the system was no longer classified as a high risk between 2015 to 2023, which meant it was not reportable under the then CDSB's at-risk standard that only required reporting of extreme and high-risk systems. TMR indicated that the risk was reduced from at risk to no longer at risk because the system was deemed stable and highly available, with very few unplanned outages. The risk rating returned to high risk because TMR determined that the system was unable to meet future business needs.
Queensland Valuation and Sales Gateway System (QVAS) managed by the Department of Natural Resources and Mines, Manufacturing and Regional and Rural Development QVAS has been used since 2000. The 2012 QGCIO report flagged this system as reaching its end of life in 2020. The software provider stopped supporting QVAS in 2020, but the department first reported it as at-risk in 2023. |
Queensland Audit Office based on CDSB dataset on at-risk systems and QGCIO 2012 report.
Departments do not always submit their resources list to CDSB
Departments provide information annually to CDSB about all IT assets and services they use. This includes information about end-of-life dates and end-of-support dates. In addition to the reporting by departments on at-risk systems, CDSB could use this annual information to identify legacy systems. There are 2 entities that did not provide this information to CDSB in 2024 (2025 reporting has not been finalised at the time of this report). CDSB does not have complete information to identify systems that are approaching or past end of life.
Legacy systems in the digital projects dashboard may not appear in the at-risk dataset
The digital projects dashboard is a publicly accessible resource that contains information about digital projects across all Queensland Government departments. There are projects listed in the dashboard that address the risk of legacy systems, however departments had not included those legacy systems in the at-risk dataset.
An example of this is the International Student Management System (ISMS) project being managed by the Department of Education. The project will upgrade to Dynamics 365 from Dynamics 2011, a legacy system that the software provider stopped supporting in July 2021. The department included ISMS in the digital projects dashboard but not in the at-risk dataset.
Many legacy systems identified for replacement over 10 years ago are still in use
In 2012, QGCIO estimated that departments needed approximately $700 million per year for the following 10 years, to replace existing IT systems which would be at end of life between 2012 and 2022. Many of those systems have not yet been replaced. Figure 3B provides 5 examples of systems that departments use, were reported as needing replacement during that 10-year period, and are included in the at-risk dataset.
Agency | System | What it is used for |
|---|---|---|
| Queensland Health | HBCIS (Hospital Based Corporate Information System) | Patient administration |
| Queensland Health | AUSLAB | Pathology and forensic laboratories |
| Department of Housing and Public Works | Ellipse | Managing property maintenance and construction activities, finance, and procurement |
| Queensland Police Service | Forensic Register | Core information management relating to forensics cases |
| Department of Youth Justice and Victim Support | QUEST | Managing trust accounts for young people in detention |
CDSB dataset on at-risk systems and QGCIO 2012 report.
The $1 billion digital fund will be used for both legacy and new systems
In 2025, the Queensland Government committed $1 billion over 4 years to drive a coordinated whole-of-government approach to digital investment and IT systems. CDSB coordinates and manages the fund with oversight from the Queensland Government Digital Fund committee, comprising director-general representation from CDSB, Department of the Premier and Cabinet, and Queensland Treasury.
The funding is for strategic and targeted digital investment, with funding allocation decisions informed by defined prioritisation criteria. CDSB anticipates that investments will include both new digital capabilities as well as initiatives to address legacy systems.
Entities have several options for managing legacy systems, including replacing, enhancing, or updating the systems; implementing workarounds; or accepting the residual risks. The most appropriate option depends on the identified risks, costs, opportunities, and return on investment.
Our forward work plan has an upcoming performance audit in 2026–27: Managing legacy information technology infrastructure and systems. In that audit, we will assess how effectively selected entities are managing the risks associated with legacy IT infrastructure and systems and are planning for system improvements and enhancements.